Menu Bar
7/13/10
7/10/10
How to change the MAC address of network interfaces in ubuntu
address of network interfaces
Features
* Set specific MAC address of a network interface
* Set the MAC randomly
* Set a MAC of another vendor
* Set another MAC of the same vendor
* Set a MAC of the same kind (eg: wireless card)
* Display a vendor MAC list (today, 6800 items) to choose from
Possible usages
These are some examples:
* You’re in a DHCP network with some kind of IP-based restriction
* You’ve a cluster that boot with BOOTP and you want to have a clean set of MACs
* Debug MAC based routes
Install macchanger in Ubuntu
sudo apt-get install macchanger macchanger-gtk
Command line Examples
# macchanger eth1
Current MAC: 00:40:96:43:ef:9c [wireless] (Cisco/Aironet 4800/340)
Faked MAC: 00:40:96:43:ef:9d [wireless] (Cisco/Aironet 4800/340)
# macchanger –endding eth1
Current MAC: 00:40:96:43:e8:ec [wireless] (Cisco/Aironet 4800/340)
Faked MAC: 00:40:96:6f:0f:f2 [wireless] (Cisco/Aironet 4800/340)
# macchanger –another eth1
Current MAC: 00:40:96:43:87:1f [wireless] (Cisco/Aironet 4800/340)
Faked MAC: 00:02:2d:ec:00:6f [wireless] (Lucent Wavelan IEEE)
# macchanger -A eth1
Current MAC: 00:40:96:43:39:a6 [wireless] (Cisco/Aironet 4800/340)
Faked MAC: 00:10:5a:1e:06:93 (3Com, Fast Etherlink XL in a Gateway)
# macchanger -r eth1
Current MAC: 00:40:96:43:f1:fc [wireless] (Cisco/Aironet 4800/340)
Faked MAC: 6b:fd:10:37:d2:34 (unknown)
# macchanger –mac=01:23:45:67:89:AB eth1
Current MAC: 00:40:96:43:87:65 [wireless] (Cisco/Aironet 4800/340)
Faked MAC: 01:23:45:67:89:ab (unknown)
# ./macchanger –list=Cray
Misc MACs:
Num MAC Vendor
— — ——
065 – 00:00:7d – Cray Research Superservers,Inc
068 – 00:00:80 – Cray Communications (formerly Dowty Network Services)
317 – 00:40:a6 – Cray Research Inc.
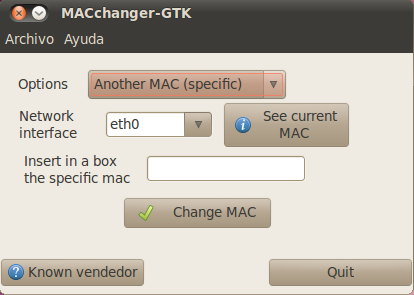
Macchanger GUI
You can open the gui by running the following command from your terminal
$ macchanger-gtk
Screenshot
Or you can do this
sudo ifconfig eth0 down
sudo ifconfig eth0 hw ether 00:a0:WH:AT:EV:ER
sudo ifconfig eth0 up
7/9/10
How to reset forgotten Ubuntu 10.04 password
It’s really easy to reset Ubuntu password! Just log in root mode. And in Ubuntu this can be done by logging in when system reboot. So we logged in CLI mode. Here’s the way, how to reset forgotten Ubuntu password. Check it out!
Login as root
There is two possible ways to login as root :
- Common method
You can login with root mode just by pressing ESC button when system starting up. That’ll take you to Grub Screen, when you can select mode that you’ll be used while booting. If you have double OS or more on your system (dual boot), you don’t need to do this step. It’s automatically go to Grub Screen when system starting up.
Then choose the “recovery mode”, usually found right below your default option. Press enter, and at the next screen, choose “drop to root sheel prompt” and you’ll login to the system as root ![]()
On some system, maybe you can’t find “recovery mode” on Grub Screen menu. So? You need to do a “little hack” to the Grub Loader. Looks cool right? In fact its very easy ![]()
On Grub Screen menu, select default loader (first choice) and press “E” key that means you’ll edit manually that loader. Wow ![]()
On the next screen, find row that contains this word :
ro quiet splash
Then replace that with this :
rw init=/bin/bash
After that, press “CTRL”+”X” (or maybe “B” key on your system, depend to your kernel![]()
) to boot the system with “hacked” loader ![]()
Done! You’re logged in as root on your system now, and you can do anything you want. Including resetting your password!
Resetting your password
Use this command to reset your password :
passwd [username]
Fill username with username that you want to reset its password. You’ll prompt new password twice.
In this step, you’re almost done! Now, make sure the change you’ve made will be written to disk by :
sync
Reboot your system :
reboot -f
You’re done! Your password has been reset, and you can login to your system now ![]()
I’ve been using this method on my Ubuntu Lucid system and its work. I hope this post is useful for you all. If you have problem when implementing this article, leave a comment and I’ll be glad to help you.
How to reset your Windows password using Ubuntu 10.04
To reset your Windows password is very easy, as easy as resetting your Ubuntu password. What you need is bootable Ubuntu system (ie. USB, CD or anything) and software called chntpw.
This is step-by-step to reset your Windows password:
- Boot from your bootable device (Ubuntu Live Session)
Shutdown your computer and boot up using your bootable system. So you run Ubuntu on Live Session that means you run your system without install it!
7/6/10
Windows Password Recovery - Windows Password Reset
One method of gaining access to the system is by trying hard to remember the forgotten password, or a password of another user which has the same level of administrative rights. However I don't think this approach will help you, otherwise you wouldn't be sitting here reading article, would you?
Another method is by trying to restore a backed up System State (in Windows 2000/XP/2003) or a ERD (in NT 4.0) in which you do remember the password. The problem with doing so is that you'll probably lose all of the recently add users and groups, and all the changed passwords for all of your users since the last backup was made.
A third method might be to install a parallel operating system on a different partition on the same computer, then use a simple trick to gain access to the old system. Read more about it on my Forgot the Administrator's Password? - Alternate Logon Trick article. For Office document password removal, you can also check our tutorials on Excel password recovery.
Note: If you are looking for password cracking tools that can be used for miscellaneous objectives such as password-protected PDF documents, zipped archives, Office documents, BIOS protection and so on then this pages is NOT for you. See some links at the bottom of this page for hints on where to find such tools, but I can tell you right away that Google might be a better choice for you.
The fourth option is by using 3rd party tools that will enable you to reset the lost password and logon with a blank password.
Update: You can also discuss these topics on the dedicated Petri.co.il Forgot Admin Password Forum.
Password Recovery Tools
Free Windows password-cracking tools are usually Linux boot disks that have NT file system (NTFS) drivers and software that will read the registry and rewrite the password hashes for any account including the Administrators. This process requires physical access to the console and an available floppy drive but it works like a charm! I've done it myself several times with no glitch or problem whatsoever.
Beware!!! Resetting a user's or administrator's password on some systems (like Windows XP) might cause data loss, especially EFS-encrypted files and saved passwords from within Internet Explorer. To protect yourself against EFS-encrypted files loss you should always export your Private and Public key, along with the keys for the Recovery Agent user. Please read more about EFS on my What's EFS? page. Out of the following list, the only tool that will no cause any harm to EFS-encrypted files on your hard disk is the Windows Password recovery system. Here are 5 of these tools:
- Stellar Phoenix Password Recovery - Simple startup utility resets a forgotten admin or users' password using a familiar Windows-like program interface instead of command-line.
- Password Kit - Top rated version of Passware's Password recovery app, supports Windows Vista and RAID/SCSI/SATA drives.
- Petter Nordahl-Hagen's Offline NT Password & Registry Editor - A great boot CD/Floppy that can reset the local administrator's password.
- Openwall's John the Ripper - Good boot floppy with cracking capabilities.
- EBCD – Emergency Boot CD - Bootable CD, intended for system recovery in the case of software or hardware faults.
If you happen to know about other free tools www.petri.co.il/feedback.htm">please let me know.
Important note for Windows Vista users: At this time there is only one solution for Window Vista and that is Petter Nordahl-Hagen's Offline NT Password & Registry Editor
Note: These password resetting tools are usually good for local users on a stand alone computer. For Domain Admin password resetting procedures please see the Related Articles section at the bottom of this page. I'd like to put together all the info you have about these issues. If you have any tips, recommended links or any ideas about how to figure out a lost password - please www.petri.co.il/feedback.htm">e-mail me and I'll get back to you.
Windows Password recovery
www.loginrecovery.com This site provides a tool to recover lost Windows XP passwords. It works for administrator and user accounts, it doesn't change the password just tells you the old one. It works with encrypted files (EFS) and password hashes. It even works if no passwords at all are known for the machine (as long as you have another computer with internet access to view this website with). Author claims it also works with Windows NT and Windows Server 2003 and Windows Longhorn, but the BEST thing about it is the fact that it won't reset your passwords, but simply reveal them for you to remember and then use. Give it a try. The author would like to receive feedback. The fee for the service is very cheap, and is really just to cover server costs. Note: You'll need a blank floppy to run the process.
Update: Author now offers the same tool as a CD image for those of you who do not have a floppy in their computer. Usage, instructions and additional information can be found at www.loginrecovery.com
Offline NT Password & Registry Editor (v080526 - May 2008)
Petter Nordahl-Hagen has written a Windows NT/2000/XP/Vista offline password editor: http://pogostick.net/~pnh/ntpasswd/
- This is a utility to (re)set the password of any user that has a valid (local) account on your Windows NT/2000/XP/2003/Vista system, by modifying the encrypted password in the registry's SAM file.
- You do not need to know the old password to set a new one.
- It works offline, that is, you have to shutdown your computer and boot off a floppy disk or CD. The boot-disk includes stuff to access NTFS partitions and scripts to glue the whole thing together.
- Works with syskey (no need to turn it off, but you can if you have lost the key)
- Will detect and offer to unlock locked or disabled out user accounts!
Caution: If used on users that have EFS encrypted files, and the system is XP or later service packs on W2K, all encrypted files for that user will be UNREADABLE! and cannot be recovered unless you remember the old password again! Download links:
- cd080802.zip (~3MB) - Bootable CD image
- cd080526.zip (~3MB) - Previous release, Bootable CD image
- bd080526.zip (~1.4M) - Bootdisk image
- drivers1-080526.zip (~310K) - Disk drivers (mostly PATA/SATA)
- drivers2-080526.zip (~1.2M) - Disk drivers (mostly SCSI)
To write these images to a floppy disk you'll need RawWrite2 which is included in the Bootdisk image download. To create the CD you just need to use your favorite CD burning program and burn the .ISO file to CD.
Support and Problems? Don't call me! Talk to the creator of this great tool. He also has a good FAQ set up covering most of the day-to-day questions. Read it right HERE. Author claims that this tool was successfully tested on NT 3.51, NT 4, Windows 2000 (except datacenter), Windows XP (all versions) and Window Server 2003. Notice that it is NOT compatible with Active Directory.
Need to change Windows NT/2000 Domain Admin password? This tool, however useful, will only reset the local administrator's password (e.g. the one found in the local computer's SAM). To reset a password of a domain administrator (or any other user for that matter) you must perform the routine that is described in the following page: Forgot the Administrator's Password? - Reset Domain Admin Password in Windows 2000 AD.
Note: The above trick will probably not work under Windows Server 2003 due to service account security changes. To work around these limitations please read the Forgot the Administrator's Password? - Reset Domain Admin Password in Windows Server 2003 AD page.
John the Ripper (v1.7.0.1)
John the Ripper is a fast password cracker, currently available for many flavors of Unix (11 are officially supported, not counting different architectures), DOS, Win32, BeOS, and OpenVMS. Its primary purpose is to detect weak Unix passwords. Besides several crypt(3) password hash types most commonly found on various Unix flavors, supported out of the box are Kerberos AFS and Windows NT/2000/XP LM hashes, plus several more with contributed patches. Read more at www.openwall.com/john. Download links: www.openwall.com/john/e/john171w.zip">John the Ripper 1.7.0.1 (1.32mb) A Pro version also exists on the author's site, however that one costs money.
EBCD – Emergency Boot CD (v0.61 - October 2004)
EBCD is a bootable CD, intended for system recovery in the case of software or hardware faults. It is able to create backup copies of normally working system and restore system to saved state. It contains the best system software ever created, properly compiled and configured for the maximum efficient use. EBCD will be very useful when you need to:
- Copy/move files (with long names, not necessary in CP437 encoding) from/to the disk but OS which can handle them (windows, Linux...) cannot boot. In particular, you may create a backup copy of normally installed and configured Windows and later restore Windows from such backup copy. So, in the case of fault OS itself and all software and its settings can be restored in 5-10 minutes.
- Perform emergency boot of Windows NT / 2000 / XP. When the loader of this OS on the hard disk is damaged or misconfigured, you are able to load OS using another, standalone loader from this CD.
- Recover master boot record of HDD. This allows to boot OS after incorrect uninstallation of custom loader (LILO, for example), which made all OS on your PC not bootable.
- Delete, move, copy to file (image) and re-create partition from file. Image transfer over network is also supported: so you may configure one PC and then make contents of hard disks of other PCs same as contents of the hard disk of the first one.
- Change password of any user, including administrator of Windows NT/2000/XP OS. You do not need to know the old password.
- Recover deleted file, even file re-deleted from Windows Recycle Bin, and, in contrast, wipe single file or a whole disk so that it will be impossible to recover it in any way.
- Recover data from accidentally formatted disk. Sometimes it helps to recover data from the disk, damaged by a virus.
- Recover data from a floppy disk, which is not readable by OS. Format 3.5" disk for 1.7 Mb size.
Also the disk includes full set of external DOS commands, console versions of the most popular archivers/compressors. Moreover, emergency boot CD includes minimal Linux distribution (Rescue Linux distribution) which may be very useful to a professional user. Read more at ebcd.pcministry.com. Download link: EBCD Pro distribution (18mb)